SecureDrive BT 1TB SSD: Hardware Review
SecureDrive BT
Summary: As secure as it gets.. for now.
5
Innovative
These days, there is an increasing need to not only be mindful of data security, but to ensure that you have an active solution to protect sensitive data. Whether it is confidential work documents or just protecting personal photographs, data encryption is becoming the norm, and moreover, preventative steps are often needed to prevent a would-be thief from accessing your data even in cases of physical theft of the disk.
Software encryption is freely available to everyone, with the likes of TrueCrypt or Microsoft Windows BitLocker, anyone could encrypt their USB flash drive or Hard Disk volume with a password and store their data with a varying degree of confidence; but that may not be suitable for businesses, or highly sensitive data, and with the recent demise of TrueCrypt in favour of BitLocker, only to see emergence of professional BitLocker cracking and recovery software that appears to be effective, better solutions are required.
SecureData Inc have developed a range of hardware encrypted external storage devices and sent us one of their new SecureDrive BT 1TB SSD external hardware encrypted disks to review, and it is quite impressive!
These products have been officially FIPS certified to a number of security standards and praised with a number of awards and positive reviews.
This drive has many features including:
- USB 3.1 / USB 2 compatible
- FIPS 140-2 Level 3 Certified
- AES256-bit XTS hardware encryption
- Unique Bluetooth lock/unlock via Android and iOS phone app
- OS independent, seen as a native drive to any OS
- Convenient unlocking: TouchID, FaceID, Face Recognition, Fingerprint unlock (Android/iOS)
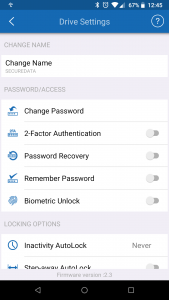
- 2-factor authentication
- Step-Away and idle auto-lock
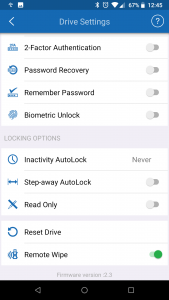
- Remote-wipe
- Read-only mode
- Brute-force auto-wipe security
Who is this for and how can it be used?
Imagine you have sensitive data, perhaps you are a government employee, member of the military, a lawyer, member of the media/press or perhaps you are a photographer or simply want to keep your information private; you have decided that you must protect this data no matter what, and you are often traveling with it, how would you keep it secure?
SecureDrive is specifically designed to provide data security by encryption, but also a level of physical security. Firstly, the USB controller is controlled by the DataLock application and is by default, locked. This means when you physically connect the SecureDrive to a computer, the drive is not exposed to the computer and cannot be mounted until you unlock it. It is simply drawing power from the USB bus and enabling the Bluetooth component only. When the password is entered and the drive unlocked, the disk will then ‘connect’ to the USB bus like any other drive.
Despite the fact that the hard disk is encrypted, if the person who stole it enters a wrong password 10 times, the disk will be auto-erased, so if the device is lost or stolen, they must have the password. But of course, what if the password is also compromised, stolen, or even your phone as well. If you had previously enabled the remote wipe feature, then the device can be remotely wiped as soon as any DataLock phone application detects the device has been connected. This means, that if somebody swipes your drive and attempts to unlock it with the correct password, you can make a reasonable attempt to protect the data. Keep in mind, that for the remote wipe to be effected, it relies on the phone unlocking the drive to be online with an active data connection in order to receive the wipe command from the central server.
In fact, this is confirmed by testing. If enabling remote-wipe, selecting remote wipe on the phone and await the confirmation message. Immediately close the DataLock App and disable mobile data and WiFi data. You can then re-open DataLock and access the hard drive with the correct key, never triggering the remote wipe. So in essence, if somebody obtains the password and the disk, and is clever enough not to unlock it with a phone connected to mobile data, then it is game over – unless you have enabled 2-factor authentication!
The disk can also be wiped quickly from the Bluetooth application, so anyone forcing you to unlock it (duress) would easily miss you hitting the erase button.
So in a practical sense, here are some real-life use cases that may suit:
- Providing the drive to a courier or errand service to deliver to a client whom knows the password/passcode
- A spy, lawyer, investigator etc, taking confidential information from A to B including through airports and checkpoints
- Employees, contractors and technicians that must take sensitive data to/from workplaces
- Confidential information that has to be stored offsite, or in a 3rd party facility, eg safety deposit box
- Secure backups or general storage drive that you don’t want others ‘borrowing’ or accidentally using. Eg, they won’t know how to ‘unlock it’ and can’t use or erase it easily.
As a hard drive
Once the hard drive is exposed to the system, it is for all intents and purposes, exactly like any other native disk. It can be formatted, partitioned and even marked as bootable like any other. If desired, additional software encryption can be applied for extra piece of mind.
Although, it is possible to install a bootable OS to the hard disk, this product would not be ideal for this purpose, because it would require the disk to be unlocked immediately during or shortly after POST, but also the disk is likely to disconnect suddenly when you walk away with your phone, or if your USB bus is unstable. But if that was the goal, stick with Linux, for obvious reasons.
The DataLock app
The DataLock app was installed and tested on Android. The app only requests location permissions on install, which should be noted. This is obviously required for the remote wipe feature and in conjunction with the additional management software.
When performing a ‘reset drive’ command, the serial number of the disk must be entered. It can also be scanned using the phone’s camera. At this time the application will also request access to the camera and camera storage.
The application is simple, easy to use, fast, and perfectly stable. Each feature when enabled has an explanative confirmation box and an opportunity to confirm or cancel the action. This is actually a good thing, because it would be too easy to accidentally wipe or turn on password recovery etc.
Feature validation
Each feature was tested individually, including the 10 incorrect password attempts. All features work as expected.
Is it really secure?
Because the hard disk is not exposed to the USB bus until it is unlocked by the app and because of the hard epoxy resign in its tamper-proof design, it is difficult to do some serious testing here. Firstly, because you can’t take the hard drive out of the enclosure and directly connect it to a SATA controller, or likewise swap the hard disk, without potentially destroying the device in the process, it is near impossible to validate the encryption, or is it?
From the FAQ page, we can deduce the following:
- No data can pass between the disk and the Bluetooth app.
- “authentication is handled via secure server/app exchange”, But “you do NOT need to be connected to the Internet or WIFI in order to unlock the drive.”
- “..absolutely no back-doors or resets. After 10 consecutive incorrect attempts the anti-hacking brute force self-defense mechanism will engage wiping all user data and drive attributes.” – and “Resetting the drive will activate a crypto erase command which will delete then regenerate the encryption key.. Even though there will be encrypted data on the drive, there is no viable way to decrypt it.”
From the specifications page:
- Immune to “Bad USB” – No firmware updates allowed
With some testing the observations made are:
- Activating a reset takes around a second.
- Brute-force reset takes around 5-10 seconds and displays “initializing encryption” during the reset.
- Mobile/WiFi data is not required for basic unlock and drive reset, but is absolutely needed for turning on 2-factor authentication and password recovery and remote wipe, and by extension, the additional remote management software.
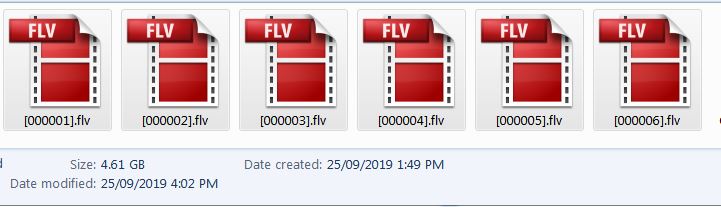
Based on this and coupled with the inability to take the drive apart, I decided to write a few GB of data and attempt a data recovery after an erase. First, a MKV movie file ~2GB was written to the disk, along with some text files. Using Recuva standalone edition, the first deep scan recovery attempt returned a result of 21 FLV files, 15 of which were 0 byte and 6 recoverable, none of which matched the file-size of any previous file written to the disk, and clearly were not actually any viable recovery of any kind.
I repeated the file recovery and found that the file size of the FLV files that Recuva had identified had grown; it was still 6 recovered FLV files but had grown to 4.61GB in step with the approximate amount of disk space that had previously been used during performance testing.
A further test was conducted, this time 41.7GB of files, approx. 49.1GB on disk was written. This represents the most amount of utilised storage ever written to the disk, so the remainder of the disk would be expected to be zeros. The recovery scan took much longer than before, but still detected the same 21 files, of which 6 were recoverable; but more importantly, the recovered data was only ~5GB.
The FLV files are not in any readable format, and when viewed by a hex editor they all contain the “FLV” as the first 3 characters, but beyond that, it looks like a bunch of encrypted data in ASCII. A further attempt using Recuva’s standard recovery method also returned all non 0-byte files of the hidden MFT structure, but these were a fresh batch from after the erase, confirmed by SysInternals NTFS tool, and in no way possessive of any meaningful data, and most importantly, the recovered data footprint in this case was only 110MB with the FLV files being 5.41GB.
Based on the official information, it confirms that the data is only “crypto-erased”, meaning that the encryption key is simply dropped and the drive volume is marked as erased. And this makes perfect sense, because a full format or data ‘erase’ always takes time, and as fast as this drive is, it cannot be ‘that’ fast.
These attempts to fully recover the encrypted data and in turn, identify the previously utilised data footprint were completely unsuccessful. The likelihood that the used data footprint could be easily revealed to a would-be thief, even after a crypto-erase, is looking highly unlikely. However, knowing that the data is still on the disk, it may not be readable now but it may be possible that the encryption could be cracked in the years to come.
So where does that leave us? Well, perhaps it is not a bad idea to use a software encryption or even file compression to have that extra layer of obfuscation if your application is sensitive enough. But otherwise, the answer is it’s secure as you can get. Although, it would not hurt to make sure that you fully zero-out the disk between owners at least.
Although, the one lacking feature and something that TrueCrypt provided for is a duress-password, Should somebody force you to provide the password, you could instead give them the duress-password which in fact initiates an erase upon entry. This is clearly something that could perhaps be easily implemented in the DataLock app. A hidden partition feature would be great too, whereby you could unlock using an alternate code to see a staged partition with files that you are happy to show others, vs the real content.
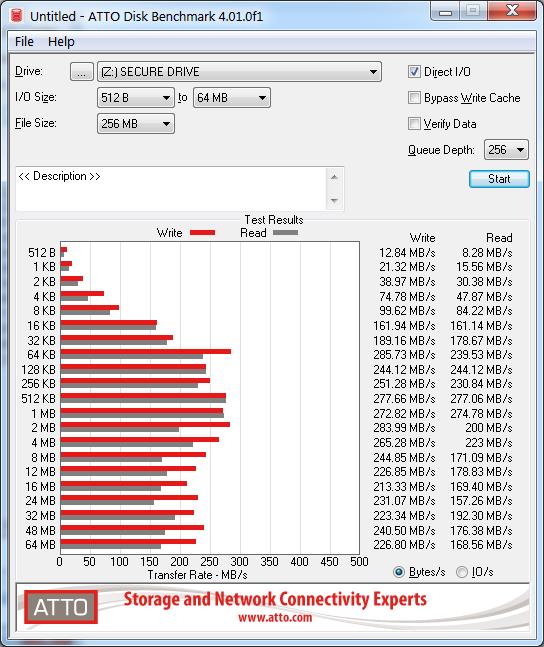
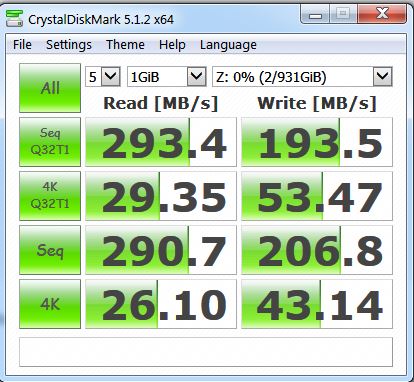
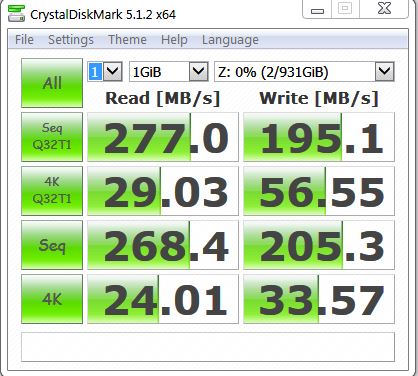
Performance
In terms of transfer rates, there were a few interesting results. Benchmarks were performed with Atto and CrystalDisk Benchmark.
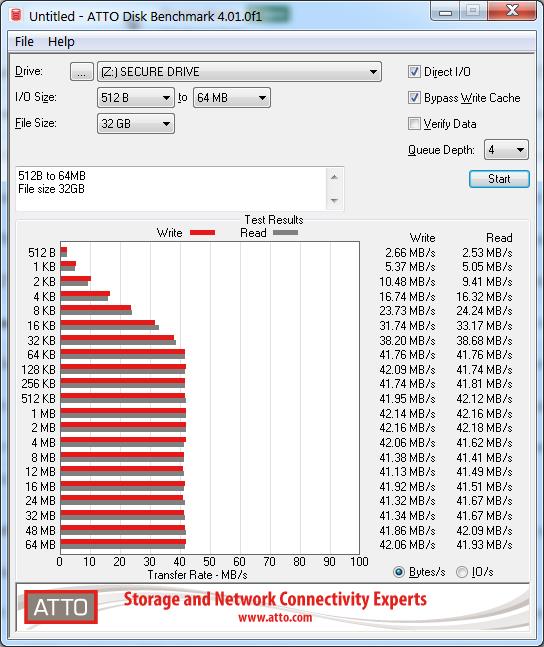
USB 2.0 transfer rate is quite consistent for read and write operations and caps out around ~50Mbps respectively.
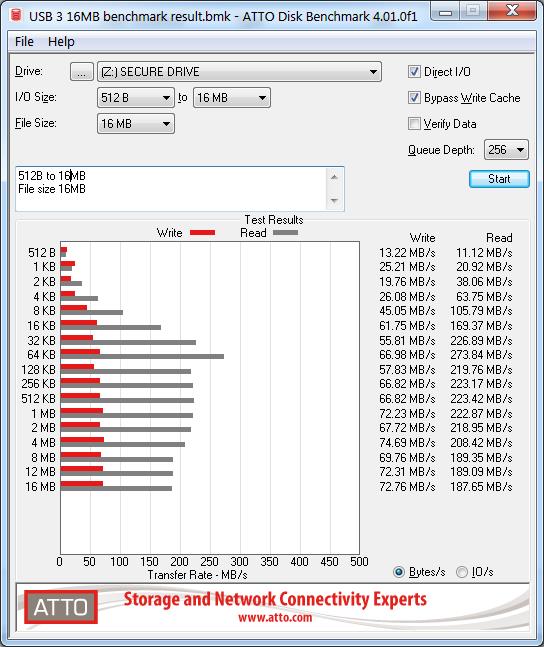
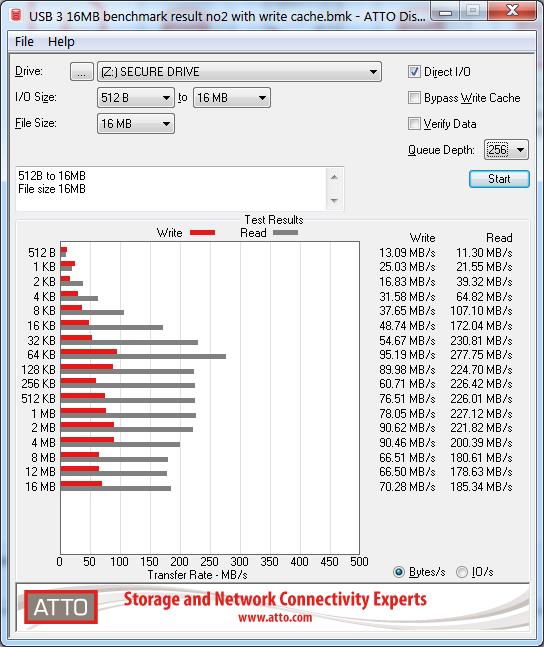
USB 3 speeds however were somewhat interesting. Several tests were performed and USB port was changed between two separate Busses. Depending upon the size of the files being transferred, the number of threads, the USB bus power/bandwidth, the source read device, a number of variables can influence the speed. Of course there is also the encryption overhead that may also be a significant factor.
Read speeds were around ~200-270MBps on average, whilst write speeds were ~100-280MBps. So the better your USB 3.1 chipset, the better your results may be.
Interestingly, copying files with Windows from a RAID 5 array often reported a transfer rate of around 450MBps and was by perception, quite fast. The 41.7GB of data mentioned earlier, took approx. 1 min 40 seconds.
Final thoughts?
SecureData’s SecureDrive BT delivers on everything it has advertised. Each feature of the phone app works perfectly as expected. The physical enclosure is both sleek and sexy and really is seemingly impossible to open without destroying it. The data really is not accessible without the encryption password.
It is also a decent external hard drive in its own right. The performance of the SSD is quite fast, with any encryption overhead being imperceptible to the user.
Only the addition of duress features such as fake partition/mounting, or fake password reset would make this product better. If this drive is used in any situation where the password can be compromised, or whereby the drive is lost, then the 2-factor authentication feature should be immediately enabled as it would be the only defense. Unfortunately, if the password and phone is obtained, then the phone PIN may be the only thing standing between the thief and your data, so again it may not hurt to have an additional software encryption in place.
All in all, this is a pretty good product and it is as safe as you will get. Just don’t let your phone go flat at the wrong time..