Leaked Emma Watson Facebook video reveals trojans, not nude pictures
Australian users among main targets
Sydney, Australia, 9th October 2014- Australian Facebook users are among the top targets of a new scam using naked videos of British actress Emma Watson as bait to spread malware, according to the Labs team at antivirus software provider Bitdefender.
According to Bitdefender Virus Analyst Doina Cosovan, the alleged sexy videos of the British actress drop more trojans than pictures and, just as in many other sex tape scams, users don’t get to see the promised content. The scam comes weeks after a hoax nude photo leak threat featuring the actress by ‘Rantic Marketing’.
“The private videos harbor several harmful trojans that solicit personal data such as phone numbers, steal tokens of legitimate apps and hijack Facebook sessions. To monetise their efforts, the malware writers also subscribe victims to premium SMS scams,” says Cosovan.
“It all starts with a Facebook comment promising to reveal private or leaked videos of Watson. The comments are automatically posted by users infected with the malware and as with many Facebook scams, victims quickly become marketers for cyber criminals.”
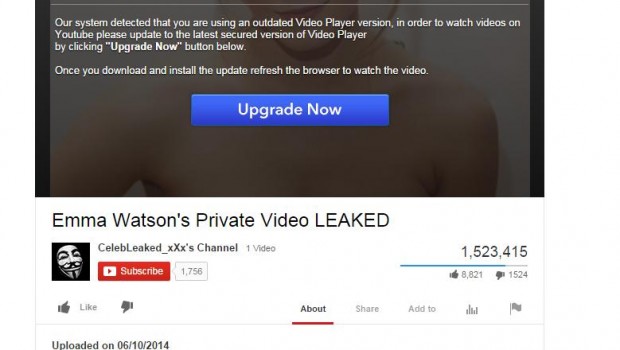
Upon clicking on the malicious links, users are redirected to a salacious YouTube copycat site before being prompted to update their Flash Player, as an error allegedly prevents them from watching the leaked videos of Watson.
The error message reads: “Our system detected that you are using an outdated Video Player version, in order to watch videos on Youtube please update to the latest secured version of Video Player by clicking [the] ‘Upgrade Now’ button below. Once you download and install the update, refresh the browser to watch the video.”
According to Cosovan, the fake YouTube account uses the Anonymous ‘Guy Fawkes’ alias to enhance credibility as the hacktivist group often claims to leak celebrity videos. The video also purports to have had more than 1.5 million likes.
In addition to stealing phone numbers through premium SMS scams, the malware disguised as a Flash Player update also changes browser settings preventing victims from seeing their list of extensions, Facebook activity and settings. Bitdefender detects the browser malware as Trojan.JS.Facebook.A, executable as Trojan.Agent.BFQZ.
“For added legitimacy, Trojan.Agent.BFQZ uses the authentic Flash Player icon and deposits the browser infection components in “C:\Program Files\Internet Explorer,” together with the install.bat, a file it also executes and adds at start up. It also takes the anti-CSRF token of the victim; a common Facebook scam mechanism. The Cross-Site Request Forgery Attack allows scammers to reuse an already authenticated session to perform unwanted actions on the user’s behalf,” says Cosovan.
“The malicious URLs also redirect users to various IP-localised surveys for added credibility whereby users can fill in the surveys in their own language. Upon clicking the “complete the survey” button however, user phone numbers are recorded and may be at risk of being sold in underground markets.”
Below are some permissions the malicious browser add-on assumes once downloaded onto victims’ computers:
- to abuse privileged paths of tabs and cookies
- to access hosts to stay in touch with the command-and-control center (one of the host websites also spreads fb-color-changer.exe, a similar malicious file that lures victims with an add-on that claims it will change their Facebook colour)
- to use scripts on “http://*/*“, “https://*/*” (and access code from other web sites)
- to steal access tokens of legitimate Facebook apps and use them to grab their permissions
- to automatically like and follow Facebook pages (which can later be monetised) to post comments on behalf of the user in every post on their timeline
In September, Watson fans were also tricked by a group of social media marketers with fake nude pictures of the British actress who created a web site titled “emmayouarenext.com,” in an attempt to shut down the 4chan website. At the time, journalists suspected the social media marketing ‘enterprise’ Rantic may itself be a hoax. In the meantime, their website went under maintenance.
All product and company names mentioned herein are for identification purposes only and are the property of, and may be trademarks of, their respective owners.